
The extended blast radius: What we know about the Nissan-Red Hat breach

Prayukth KV
23. Dezember 2025
The extended Blast Radius: What we know about the Nissan-Red Hat breach
Modern threat actors and data thieves no longer view the enterprise as a monolith. Instead, they apply a clinical taxonomy to their targets, systematically triaging an organization’s assets into four (initial) strategic domains of interest. This includes Customer Trust (PII), Internal Stability (Employee Data), Intellectual Capital (Enterprise Data), and most critically, Functional Sovereignty (Operational Control)." This makes it easier to figure out attack paths and harvest the relevant data bits with more focus, attention and tactics.
In the automotive world populated by high-stakes technology, we often talk about cybersecurity within the "perimeters" of our business and treat them as if they were solid walls. Enterprises also invest millions in firewalls, EDR, and SOCs to secure their internal gates. However, as the recent breach involving Nissan and Red Hat demonstrates, the modern enterprise certainly has no walls. Instead it has a well networked circulatory system extending all the way to external consultants who are supposed to be temporary guardians of data. And when a major artery like a global consulting partner gets nicked, the impact of a leak (no matter how small) can be felt thousands of miles away.
The timeline of the attack
Somewhere on the morning of September 26th which was a Friday, the attack in the form if unauthorized access was first detected by Red Hat. Acting immediately, RedHat blocked access to the data and isolated the server to prevent any further access to the server even from validated sources.
A week later and after a round of internal confirmations, RedHat passed on the information on the breach to Nissan on October 3rd (the Friday after) who immediately reported the breach to Personal Information Protection Commission. In addition, as per Nissan, they also contacted customers who are believed to have been impacted by the breach directly or who data was compromised in the breach. The company also issued an apology on its website.
The impacted server was not known to contain any other information than the breached data as per Nissan.
The anatomy of the Nissan attack and its aftershock
When viewed from a stratospheric level, the news is a standard data breach headline: 21,000 Nissan customers in Japan had their personal details exposed including customers who have (or had) purchased vehicles and entered services at the former Fukuoka Nissan Motor Co., Ltd. (currently Nissan Fukuoka Sales Co., Ltd.)
But the source of the leak wasn't an unsecured or forgotten Nissan server. The incident involved a routed indirect hit on Nissan that possibly originated from a compromised GitLab instance that was used by Red Hat Consulting. The levels of data protection accorded to the server are unknown at this point.
The so called "Crimson Collective" the threat actor behind the breach didn't just steal records. They stole 570GB of "Customer Engagement Reports" (CERs) numbering around 800.
As per the automotive major, Nissan's customer engagement strategy focuses heavily on personalized mobile messaging, a seamless digital-to-dealership experience, and using data analytics to deliver relevant content and services. The company aims to build long-term loyalty and achieve high conversion rates and it is possible that this data was collected and stored as part of this exercise and handed over to Red Hat as part of a project.
The stolen reports contain details such as:
· Verified full names
· Physical addresses
· Phone numbers
· Email addresses
· Customer data used in sales and insurance related operations
The company has claimed that credit card details were not part of the breach. Nissan has also issued an advisory to impacted customers to be careful about responding to suspicious calls about their vehicles.
When blended with other information that could be sourced from stolen databases, this could easily bring the customers a step closer to a breach in a phishing attack. This data could also be used to build a buyer profile of the customer and it's essentially a downhill from here.
The "Consultant Blind Spot"
Nissan had multiple collaborative projects with Red Hat.
As per available information, Nissan had engaged Red Hat with a consultancy opportunity to transform the automotive major into a key player in the software-defined vehicle space. This was a data heavy collaboration. Nissan had in fact announced that it would be using the Red Hat In-Vehicle Operating System to power its next-generation software-defined vehicle platform. As per Red Hat, its new vehicle operating system can support advanced driver-assistance systems, digital cockpits, telematics, infotainment, and cutting-edge AI models.
In addition to this, Nissan had also engaged Red Hat to build a customer management system. Details of this project are not very clear. From available information made available to us and analysed by our research team, it seems that it was this project that was impacted by the breach.
The data leaked was information given to Red Hat's consultants by Nissan for the purpose of working on the customer management system project. Red Hat's consultation division had stored the information on its own internal GitLab instance alongside the project's other artifacts. Unfortunately, this was the very server that was breached. So technically this is not a breach at Nissan.
For years, I have argued that consulting firms are turning into ultimate credential aggregation points. We hire experts to help us scale, but in doing so, we often grant them a level of trust that bypasses our standard Zero Trust protocols. Such a dichotomy in security controls could easily be misused by a threat actor. In fact threat actors do keep an eye out for consultants that handle such data. This is not to blame anyone here in any manner. But this is a standard practice across industries that operates based on the level of trust that exists between the client and the consultant (in some cases the consultant could even be an individual).
When a consultant creates a "shadow repository" or a test environment to build your next customer engagement management system, that environment could sit well outside the rigorous oversight of your internal CISO or the security team concerned. In some cases, it may not even be subject to the same risk assessment audits that other bits of your infrastructure are subject to. There have also been instances in the past when a collaboration ends but the consultant retains the client's data for a while. Sometimes the data is even forgotten in the process.
An additional layer of security for such data and collaboration could go some way in helping in preventing such incidents.
Three lessons for the strategic cybersecurity leader
If you are sitting in a boardroom today, the Nissan-Red Hat event should trigger three immediate shifts in your thinking:
Start auditing engagements: We spend months vetting a software vendor’s product but only minutes signing a SOW for their consultants. We must treat consulting teams as privileged users with "permanent-temporary" access that requires continuous, automated monitoring. The consultant should furnish compliance reports on an ongoing basis for meeting the risk exposure needs of the customer.
The death of static secrets: Hardcoded secrets in Customer Engagement Reports (CERs) were the primary fuel for this breach. In an era of AI-driven threat hunting, static tokens are a liability. If a secret can be written down, it can be stolen.
Recognize the extended "Blast Radius": This breach affected Nissan, but the stolen data included reports for over 800 organizations, including government agencies and financial giants. We must map our "blast radius" and know the answer to the question “if our primary consultant is breached tonight, what specific keys to our kingdom do they currently hold”?
The big picture. Looking beyond the firewall
At Shieldworkz, we often discuss the convergence of the digital and physical. In the automotive sector, this isn't just about "customer names". Instead, it's about personal data of the customer and the infrastructure that manages the vehicle's lifecycle. As we move toward smarter, connected cities, a breach of a "customer management system" even at a pilot project level can be the first step toward a much more dangerous intrusion into the OT (Operational Technology) layer of our lives.
Security is no longer a technical problem; it is essentially an ongoing intellectual awareness challenge. It requires the imagination to see the connections we’ve built and the courage to secure them even when they are out of our direct sight.
Is your organization’s consulting layer a well supervised bridge or a breach waiting to happen?
And finally, new rule (in Bill Maher's voice): Treat your third-party consultants not as "trusted guests," but as a critical extension of your attack surface that requires the same Zero Trust rigor as your internal teams.
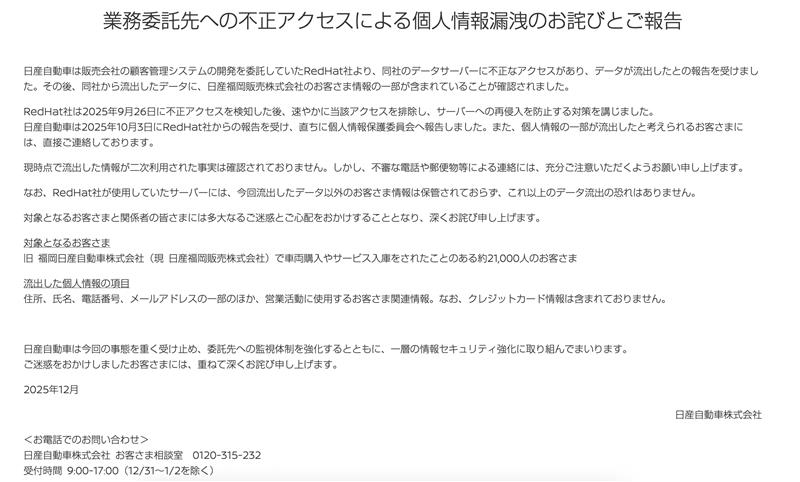
A note on the breach put out by Nissan earlier today
Wöchentlich erhalten
Ressourcen & Nachrichten
You may also like
11.02.2026
CISA’s advisory for critical infrastructure operators to enhance secure communications

Prayukth K V
09.02.2026
How a side-hustle paralyzed Romania’s national oil pipeline

Prayukth K V
05.02.2026
A deep dive into 2025's most devastating cyberattacks as per Tokio Marine HCC International

Prayukth K V
03.02.2026
Achieving NIS2 compliance via the IEC 62443 framework

Prayukth K V
03.02.2026
NERC CIP Roadmap for 2026: Practical Steps for Power Generation to Protect PLCs and RTUs

Team Shieldworkz
28.01.2026
Observed reduction in Chinese APT Operations amid 2026 PLA purge

Prayukth K V












