

Prayukth K V
December 25, 2025
As families across France prepared for the 2025 holiday season, a different kind of "package" was delivered at the headquarters of La Poste. Just days before Christmas, on December 22, the nation’s postal and banking giant was hit by a massive cyberattack. This one did way more than just crash a website. It actually weaponized the year's busiest logistics window for some form of geopolitical gain.
On December 22, the organization’s website uploaded a brief message that opens “Notre site est indisponible” or our site is unavailable. It added that La Poste teams are doing eveything they can to resolve the situation quickly.
Further, on its Facebook page, La Poste published anothernotice that stated “A major network incident is currently disrupting all of our information systems.”
The notice stated that the laposte.fr site is down right now, as is the Digiposte secure document storage service, La Poste’s digital identity service, and the La Poste app.
The notice also warned that some post offices could experience some level of degraded service. It however stated that over-the-counter transactions remain possible.
La Poste also operates a bank, Banque Postale, which is experiencing trouble.
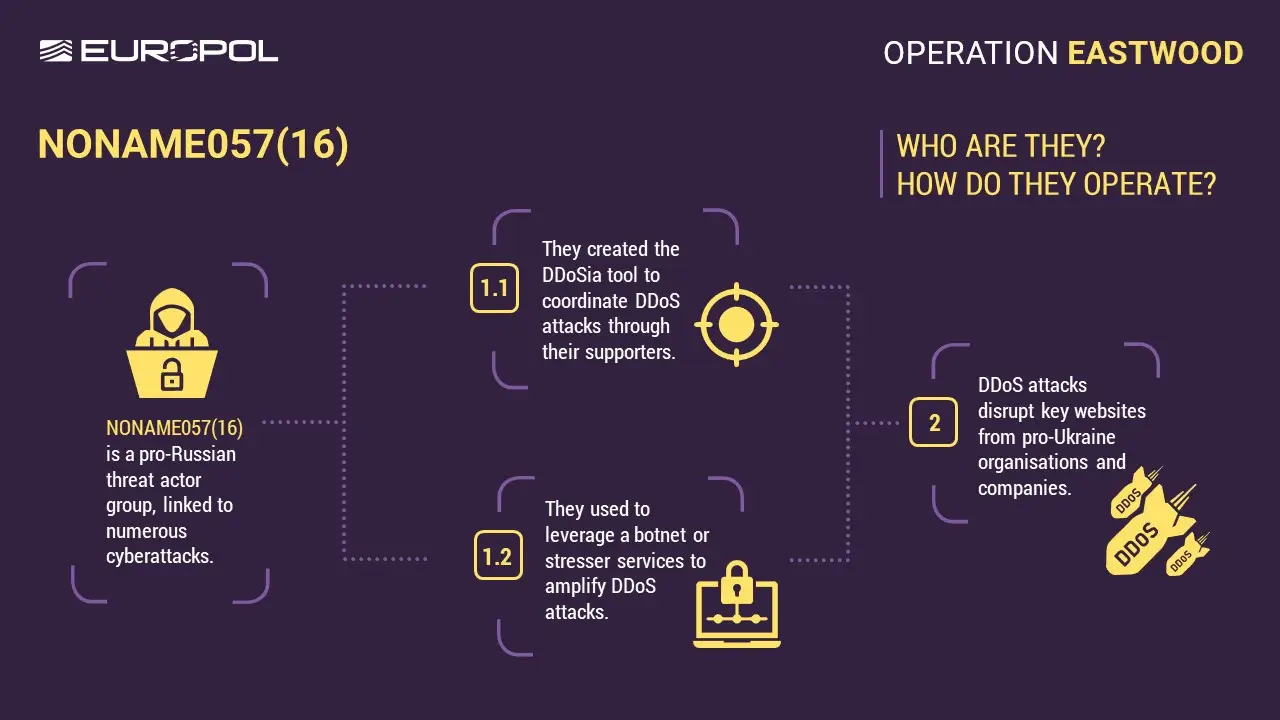
Pro-Russian Hacktivist Group NoName057(16) that claimed the attack is a known threat actor that has been targeting NATO and Ukrainian cyber assets. The timing of the attack and choice of La Poste offer many clues on the motivations behind the attack and the timing is not coincidental. Instead it seeks to serve a year-end reminder of the nuisance value that such groups backed by nation states hold.
In today’s blog post, we take an inside look at the attack, the suspects, and what this means for the future of hybrid warfare.
But before we move forward, don’t forget to check out our previous blog on “What we know about the Nissan-Red Hat breach” here.
Let’s dive in.
The weapon of choice
The attack has been identified by Shieldworkz researchers as a Distributed Denial of Service (DDoS). Unlike a ransomware attack that steals data for a fee, a DDoS attack is designed to overwhelm a system with sheer volume. This is often a preferred mode for hacktivist groups that wish to leave a message behind without asking for ransom or get into any form of negotiation with the crooks behind a cyberattack. Sometimes such attacks are also used to:
· Test the defenses of an organization
· Identifies possible windows for data exfiltration
· Checks employee competencies
· Grades incident response capabilities of an organization
All this is done to create grounds for more accurate and targeted attacks in the future.
Coming to what happened on December 22, by flooding La Poste’s DNS (Domain Name System) servers with illegitimate traffic, the hackers effectively "locked the front door" to the company’s digital services.
The Impact: While physical letters were not impacted from a delivery standpoint, the digital brain managing operations was effectively paralyzed.
The casualties: Package tracking went offline, the La Banque Postale app (that the time of writing this piece was serving nearly 11 million people) went silient, and the Digiposte document vault became inaccessible.
The culprit: NoName057(16)
The pro-Russian hacktivist group NoName057(16) has already claimed responsibility for the incident. This group has become a persistent thorn in the side of NATO nations and allies. Emerging shortly after the 2022 invasion of Ukraine, they specialize in "propaganda through disruption."
By targeting La Poste, the group isn't just seeking data; they are also seeking visibility and attention within Russia and outside. Their goal is to create a sense of digital insecurity in Western societies, punishing France for its continued military and political support of Ukraine.
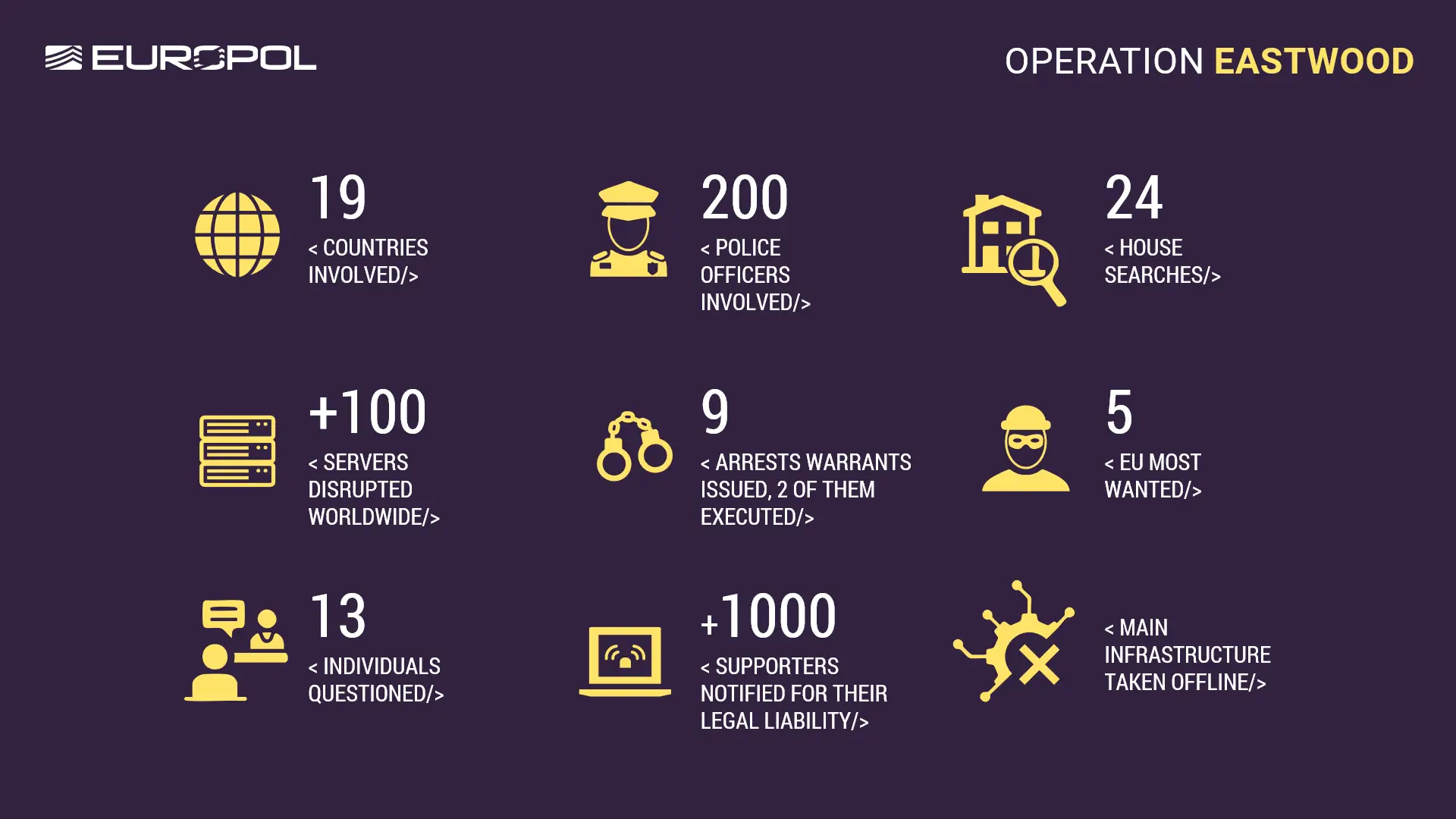
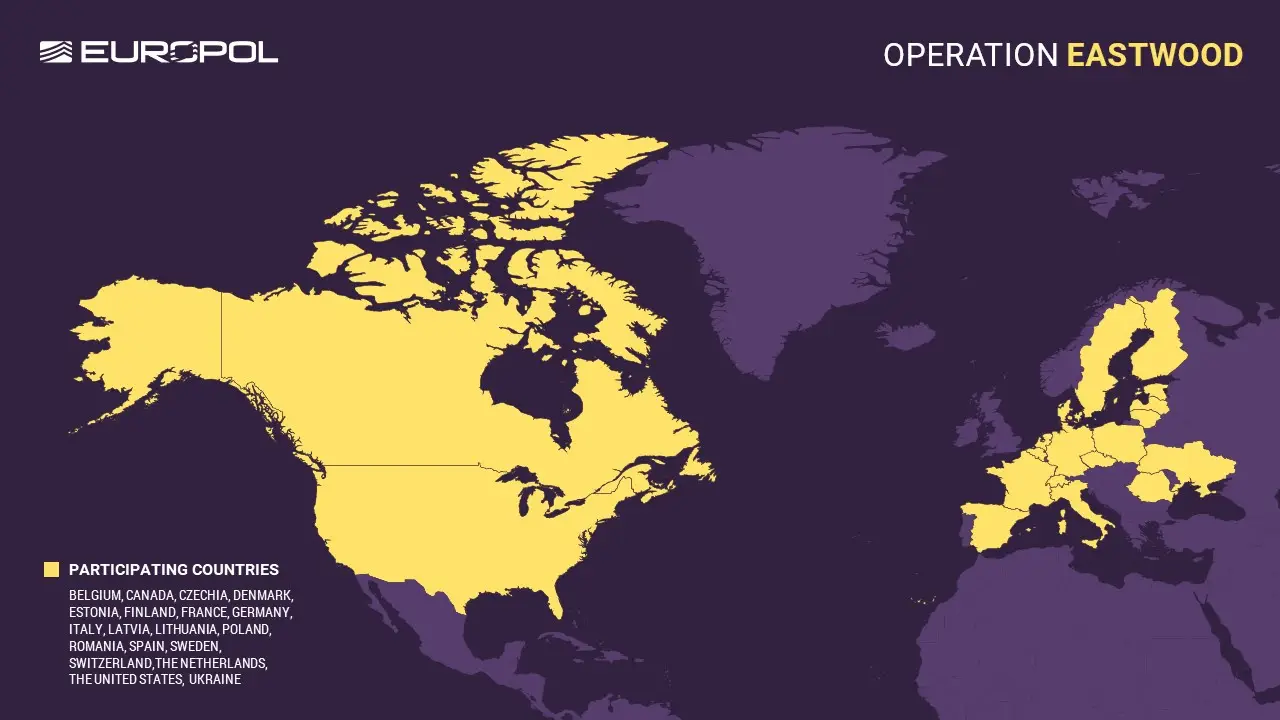
It may be remembered that between 14 and 17 July, a joint international operation, known as Operation Eastwood and coordinated by Europol and Eurojust to target the cybercrime network associated with NoName057(16) was launched. Law enforcement and judicial authorities from Czechia, France, Finland, Germany, Italy, Lithuania, Poland, Spain, Sweden, Switzerland, the Netherlands and the United States took simultaneous actions across jurisdictions against cyber criminals and infrastructure belonging to the pro-Russian cybercrime network. The investigation was also supported by ENISA, as well as nations such as Belgium, Canada, Estonia, Denmark, Latvia, Romania and Ukraine. The private parties ShadowServer and abuse.ch also assisted by chipping into support the technical part of the operation.
This campaign led to the disruption of an attack-infrastructure put together by the group. This included over one hundred computer systems and networks worldwide. A major part of the group's central server infrastructure was taken offline. Beyond the effort, Germany issued six warrants for the arrest of offenders living on Russian soil. Two of these persons were accused of being the main instigators responsible for the activities of "NoName057(16)". These people could have been the handlers of the actual hacktivists or coordinators. Either way these were the proverbial big fish.
In total, national authorities issued seven arrest warrants in July, which were directed, inter alia, against six Russian nationals for their involvement in the operations of NoName057(16). All of the suspects have since been listed as internationally wanted, and in some cases, their identities were released to the media in order to engage citizens in reporting the activities of these criminals. Profiles of five NoName057(16) cybercrooks were also published on the EU Most Wanted website.
National authorities since then reached out to many individuals believed to be underground supporters of this cybercrime network. The messages were sent via a popular messaging application, to inform the recipient of the official measures highlighting the criminal liability they bear for their actions pursuant to national legislations.
It was then reported by Europol that individuals acting for NoName057(16) are mainly Russian-speaking sympathisers who use automated tools to carry out distributed denial-of-service (DDoS) attacks. Operating without formal leadership or sophisticated technical skills, they are motivated by ideology and rewards.
Despite this operation, it seems that NoName057(16) has been resurrected and is now in a state wherein it can conduct operations. How did that happen? We have a theory for that as well. I will reveal that bit towards the end.
Why now? The strategic timing
In the world of cyber-warfare, timing (more often than not) is everything.
Logistical stress: La Poste sorts and delivers over 2 million items daily in the run-up to Christmas. By disabling tracking and online payments, the hackers forced a return to manual processing, creating a massive bottleneck. Besides, it also led to La Poste requestioning the services of additional employees to manage the stress.
Psychological impact: By targeting a service as "homely" and essential as the post office during the holidays maximizes public frustration. It turns a technical glitch into a national conversation at the dinner table.
Year-end reminder: While the operation to wipe out the group was carried out in July, NoName057(16) wanted to convey a message to the law enforcement machinery of EU that it is very much around and willing to engage in more disruption.
The broader context: A "wave" of attacks
This incident certainly wasn't an isolated event. It capped a month of escalating geo-political and digital tension in France:
The Interior Ministry: A separate breach recently compromised sensitive files.
Maritime Security: Remote access malware was recently discovered on a passenger ferry.
Public Services: France Travail (the employment agency) has faced repeated attempts to compromise citizen data.
Geopolitically, the strong stand taken by the French government on Ukraine has brought France into the crosshairs of Russian cyber criminals and their state-backed handlers. France is also actively working to bring more security guarantees for Ukraine.
French intelligence (the DGSI) has officially taken over the probe, signaling that the state views this as a matter of national security rather than a simple corporate IT failure.
Lastly you may we wondering how NoName057(16) has been able to resurrect itself so quickly. The answer is simpler than you can imagine. State-backed actors maintain a steady pipeline of resources and people to continue operations in case of a disruption. These resources are scattered at locations such as North Korea and Iran where they are immune from any form of legal action. Once the threat actor playbooks are mature and the TTPs are framed, then it doesn’t matter where the group operates from or what kind of an action it is subject to. The hacktivist or threat actor is able to bounce back within a very short period of time under a new identity or using new members.
Such an approach ensures continuity of operations and learning for the threat actor and it’s handler.
The bottom line
The 2025 La Poste attack proves that hackers do not celebrate holidays or take the time out during lean work season. It also proves that critical infrastructure continues to be a sitting duck for cyber crooks bent on creating disruption. As we come closer to 2026, the challenge for nations such as France and for the EU will be building "digital redundancy" and ensuring that when the cloud goes dark, the country can still function.
Interested in a custom briefing on NoName057(16)? Talk to our expert.
Test drive our NDR solution for OT security, here.
For everything else, let us know here.
Data about Operation Eastwood sourced from Europol
The image used is for representative purposes only.
Get Weekly
Resources & News
You may also like
Feb 11, 2026
CISA’s advisory for critical infrastructure operators to enhance secure communications

Prayukth K V
Feb 9, 2026
How a side-hustle paralyzed Romania’s national oil pipeline

Prayukth K V
Feb 5, 2026
A deep dive into 2025's most devastating cyberattacks as per Tokio Marine HCC International

Prayukth K V
Feb 3, 2026
Achieving NIS2 compliance via the IEC 62443 framework

Prayukth K V
Feb 3, 2026
NERC CIP Roadmap for 2026: Practical Steps for Power Generation to Protect PLCs and RTUs

Team Shieldworkz
Jan 28, 2026
Observed reduction in Chinese APT Operations amid 2026 PLA purge

Prayukth K V












