

Prayukth K V
January 2, 2026
As 2025 came to an end a few days ago, the last major cyberbreach of that year was revealed. On December 26, 2025, a threat actor known simply as “888” put stolen data from the European Space Agency (ESA) on the digital auction block. The threat actor claims to have exfiltrated over 200 GB of internal data.
Just 4 days later, on December 30, 2025, the ESA officially confirmed the breach. While the agency has categorized the actual impact as “limited” to few external, unclassified servers, our research suggests that the "blast radius" could be far more significant than a few leaked schematics.
The anatomy of the breach: What went wrong?
The ESA’s initial statement emphasizes that the compromised systems were limited external servers supporting collaborative engineering. However, when it comes to data, for a space agency, the line between "external collaboration" and "mission-critical" could be increasingly blurred especially when it comes to critical missions involving multiple sub projects and collaborations.
What was stolen?
As per the threat actor, the stolen data includes source code files, CI/CD pipelines, API and access tokens, confidential documents, configuration files, Terraform files, SQL files, hardcoded credentials, and private Bitbucket repositories.
Our analysis of the leaked samples and an analysis of the actor's claims reveals a possible failure at the intersection of identity management and third-party collaboration tools.
The entry point: The attacker is said to have gained access on December 18, 2025, and was able to maintain a foothold for a duration of an entire week.
Targeted platforms: The breach was focused on Atlassian’s suite elements specifically Jira and Bitbucket. These are the "nervous systems" of modern engineering, used to track bugs, manage tasks, and store source code.
The "Shadow" Infrastructure: Available clues point to a potential compromise of CI/CD pipelines (Continuous Integration/Continuous Deployment) and Terraform files.
If the hacker gained access to Terraform code, it is possible that they didn't just get some basic data. Instead, they could very well have got the architectural blueprint of ESA’s cloud infrastructure. This could allow an adversary to see how servers are provisioned, where the firewall rules are weak, and how to potentially pivot into deeper networks.
Threat actor profile: Who is hiding behind "888"?
The threat actor hiding behind the pseudonym "888" isn't new to the cybercrime underground. This threat actor has rapidly ascended the ranks of BreachForums since early 2024. Here are a few details on some of the cyber incidents claimed by the group.
Attribute | Details |
Known History | Linked to breaches of Shopify, Decathlon, and HPE (boasted in early 2025). |
Tactics (TTPs) | Heavily relies on stolen credentials (likely sourced from infostealer logs) and exploiting misconfigured API tokens. |
Motive | Primarily financial. The ESA data is being sold for Monero (XMR) to ensure anonymity. |
Sophistication | Moderate to High. They aren't just "smash and grab" artists; they know how to navigate development environments like Bitbucket to find the highest-value assets (keys and tokens). |
During the Shopify related breach, 888 claimed to have stolen a huge cache of data from a compromised third-party app. Subsequently, on July 3, 2024, "888" offered a database for a one-time sale using the anonymous cryptocurrency Monero (XMR). The data contained around 180,000 rows of user information, including:
· Shopify ID
· First and last names
· Email addresses
· Mobile phone numbers
· Order counts and total amount spent
· Email and SMS subscription details
Shopify denied any breach in its core systems.
Earlier in May 2024, 888 had claimed to have breached Decathlon. The target was Decathlon Spain and the breach impacted nearly 6600 employees.
Forensic update: The "codebase" compromise
The targeted repositories
An initial analysis of the screenshots and directory structures shared by the threat actor points to the compromise of private Bitbucket instances specifically linked to Open Science and Collaborative Engineering. While these are mostly "unclassified," they do house the logic and plumbing for several high-profile initiatives that include (but are not limited to):
Earth observation (EO) processing pipelines: The leak seems to include Python and C++ source code for data ingestion and calibration. This could likely impact components of the Copernicus programme (specifically Sentinel-related data processing) where external university partners contribute to the code.
Infrastructure-as-Code (IaC) Assets: Most alarming are the Terraform and Ansible files. These are not just "documents". Instead, they are the instructions used to assemble ESA's cloud environments. If an attacker gets their hands on these, they can potentially understand the exact network topology (including additional security measures), the IP addresses of internal gateways and the types of encryption used for data-at-rest.
CI/CD Pipeline Configurations: The exfiltration of Jenkins and GitHub Action/Bitbucket Pipe configurations suggests that "888" had some degree of visibility into how ESA validates its software. This creates a "long-tail" risk of logic-bomb injections in future software updates.
Missions at risk?
Though ESA has not released a specific "list" of missions, the platforms compromised (Jira and Bitbucket) are the primary coordination hubs for:
Hera and planetary defense: Collaborative missions involving international partners frequently use these "science-DMZ" servers for task tracking and code sharing.
Space safety and debris removal: Projects like ClearSpace-1 involve heavy external engineering coordination, making them prime candidates for the "collaborative science" servers ESA mentioned.
Horizon Europe Space Research: Any unclassified research funded by the EU and managed by ESA often resides on these specific external-facing development servers.
"888"'s strategy: A data broker’s endgame
Unlike "smash-and-grab" ransomware groups, 888 also functions as a high-end data and compromise broker. Their reputation on the dark web that was built on previous breaches of Shopify, Decathlon, and HPE is based on the authenticity of their samples.
Monero (XMR) Exclusive: The demand for Monero suggests the actor is looking for a clean, untraceable exit. No surprises here.
The "Silent Buyer" Risk: There is a high probability that the 200 GB won't be leaked publicly but will instead be sold to a state-sponsored entity (APT). For a nation-state, "unclassified" telemetry formats and satellite command structures are "zero-day" intelligence.
Rogue nations could potentially use this data to augment their capabilities around payload delivery in space, earth observation systems, internal collaboration on projects and for smaller projects linked to dual use technologies.

Future risks and threats
The ESA has maintained that no classified systems were affected in the incident. However, in the world of orbital mechanics and satellite defense, even unclassified data offers a goldmine for secondary exploitation.
The Telemetry treasure trove
The breach reportedly includes telemetry datasets and simulation models. While not "Top Secret," this data provides adversaries with the exact operational parameters of ESA satellites. Knowing the precise fuel consumption or thermal tolerances of a satellite allows a hostile actor to plan "non-kinetic" interference (e.g., signal jamming or laser dazzling) with pinpoint accuracy.
The hardcoded credential-related challenges
The attacker has claimed to have seized hardcoded credentials and API access tokens.
The risk: These tokens act like "skeleton keys." Even if the ESA secures the initial server, a single forgotten token in a private repository could allow "888" (or whoever buys the data) to re-enter the network months later.
Supply chain vulnerability
By leaking CI/CD pipeline configurations, the actor has exposed how the ESA builds and deploys its software. This opens the door for a SolarWinds-style supply chain attack, where a malicious update could be injected into future mission software before it ever leaves the ground.
ESA has taken many steps to augment its security posture in the past and remains committed to securing its infrastructure from bad actors. The agency’s newly inaugurated state-of-the-art Cyber Security Operations Centre (C-SOC) in Germany that is supposedly leading the forensic cleanup is one such measure. There is always room for improvement and a unified Zero Trust approach covering all parts of the infrastructure could be a strong measure in this direction.
More about our NIS2 compliance services.
Learn a bit more about Shieldworkz’ Incident response services
Talk to a vacation security expert (yes we have a dedicated security pro who knows more about fine tuning your security measures during lean times).
Test drive our OT security platform here.
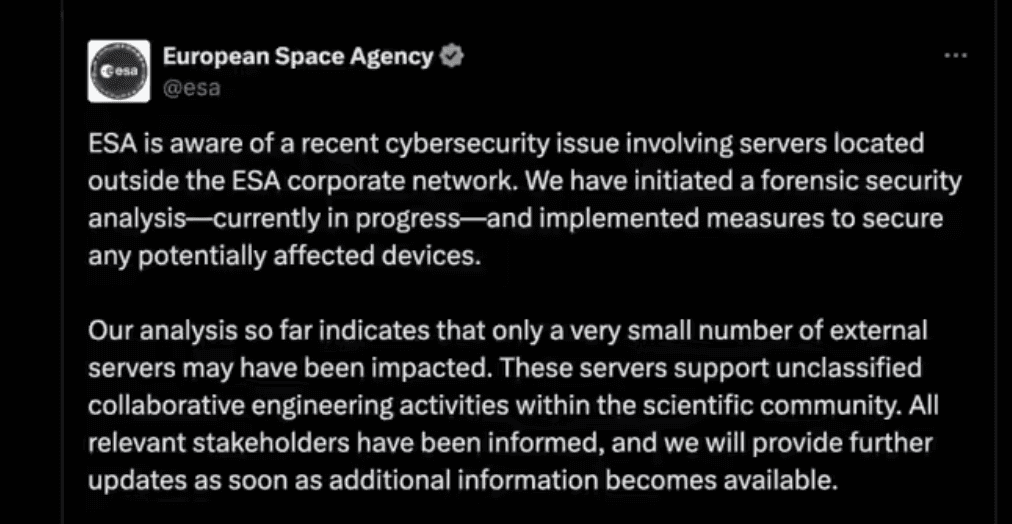
A note on the breach issued by ESA
An initial analysis of the screenshots and directory structures shared by the threat actor points to the compromise of private Bitbucket instances specifically linked to Open Science and Collaborative Engineering.
Get Weekly
Resources & News
You may also like

Mar 3, 2026
How the Iran crisis is impacting cyber space

Team Shieldworkz

Mar 2, 2026
Cyber threats in the Middle East: What organizations need to know right now

Team Shieldworkz

Feb 27, 2026
Building an OT Cybersecurity Program with IEC 62443 and NIST SP 800-82

Team Shieldworkz

Feb 25, 2026
All about the new EU ICT Supply Chain Security Toolbox

Prayukth K V

Feb 24, 2026
AI and NERC CIP-015: Automating Anomaly Detection in Critical Infrastructure

Team Shieldworkz

Feb 23, 2026
Using the IEC 62443 framework to comply with NIST SP 800-82: A CISO's guide

Prayukth K V







